
If your business accepts credit card payments, you know that PCI DSS compliance isn’t optional—it’s required. And if you’ve ever tackled the quarterly external vulnerability scans required by PCI DSS, you’ve probably realized: passing an ASV scan sounds straightforward, but in practice, it’s easy to trip up. For many organizations, those scans become a source of stress and uncertainty—one more thing to worry about in an already packed security schedule.
If you’ve ever had a scan come back with a big, red “FAILED” across it, you’re not alone. Repeated ASV scan failures are more common than you might guess. Besides delaying compliance, these failures can mean extra expenses and, in some cases, put your ability to handle card payments on the line. The good news? Most problems that cause ASV scan failures are absolutely manageable—with the right planning, you can turn scans from a dreaded checkbox into a powerful security tool.
Let’s break down why organizations typically stumble—and the practical steps you can take, based on real challenges and solutions, to not just pass but thrive.
Bottom line: Treat ASV as a continuous security habit—not a quarterly scramble—and your pass becomes the natural outcome.
The Real Purpose of ASV Scans in PCI DSS Compliance
PCI DSS (Payment Card Industry Data Security Standard) lays out strict requirements for any company that stores, processes, or transmits cardholder data. One big requirement is the quarterly vulnerability scan by an Approved Scanning Vendor, or ASV.
Now, this isn’t just “run a scan and forget about it.” The scan checks your internet-facing assets—the windows and doors to your digital house—for weaknesses that could let attackers in. The ASV is basically your security inspector, using specialized tools to look for cracks in the foundation.
What do you need for a “pass” on your report? Three things, every time:
- You scan everything in scope: That means every server, every domain, all your public IPs, even those temporary cloud resources that someone spun up for a project and forgot about.
- No big vulnerabilities remain: Anything scored as “high risk” (CVSS of 4.0 or above) must be fixed first.
- The report is squeaky clean: No unsupported software. No obviously insecure settings.
For organizations that are moving fast—wrestling with cloud shifts, constant upgrades, or busy DevOps teams—keeping up with these basics can feel like playing whack-a-mole.
Free ASV Scope & Readiness Call
15–20 minutes to confirm scope, avoid false fails, and plan a clean first pass.
Why Do So Many Companies Fail ASV Scans?
It’s usually not one giant blunder that leads to a failed scan. It’s the little things that sneak through the cracks—missing information, process gaps, or tech oversights. Here’s what we see most often:
-
Overlooked Assets and Incomplete Scopes
Ever find out there’s a server or API exposed to the internet that nobody told you about? You’re not alone. As companies move faster, embracing cloud adoption and spinning up new resources quickly, the risk of missing something grows. Missed assets mean incomplete scans—and those will never fly when it’s time for compliance. -
Outdated Software and Missed Patches
This one hurt because it’s so preventable. An old Windows server buried in a backup data center, or a forgotten plugin on your marketing site, can derail your scan. Attackers love these “low hanging fruit,” and so do ASVs—any unsupported operating system or unpatched vulnerability is an instant red flag. -
Weak Configurations Open the Door
Maybe you have up-to-date software, but if you’re still using outdated SSL protocols or left a default password on your router, you’re creating risk. Common configuration mistakes include:- Obsolete protocols (e.g., TLS 1.0/1.1)
- Weak cipher suites
- Open but unnecessary ports
- Default/weak creds
-
Band-Aid Fixes and Recurring Vulnerabilities
How many times have you fixed something just for the next scan to bring it right back? Quick patches before the ASV arrives might clear the latest hurdle but don’t deal with the root cause. If a port is open because of a misconfigured automation script, simply closing it doesn’t solve the real problem. Expect that vulnerability to pop up again. -
No Clear Ownership
Who’s in charge—the IT team, the compliance group, your security manager? When responsibilities aren’t clear, things get missed. Remediation gets delayed, deadlines loom, and the scramble begins. This reactive approach makes each scan more stressful than the last.
Need a Zero-Surprise ASV?
We’ll pre-scan, prioritize fixes, and coordinate scanning windows with your change schedule.
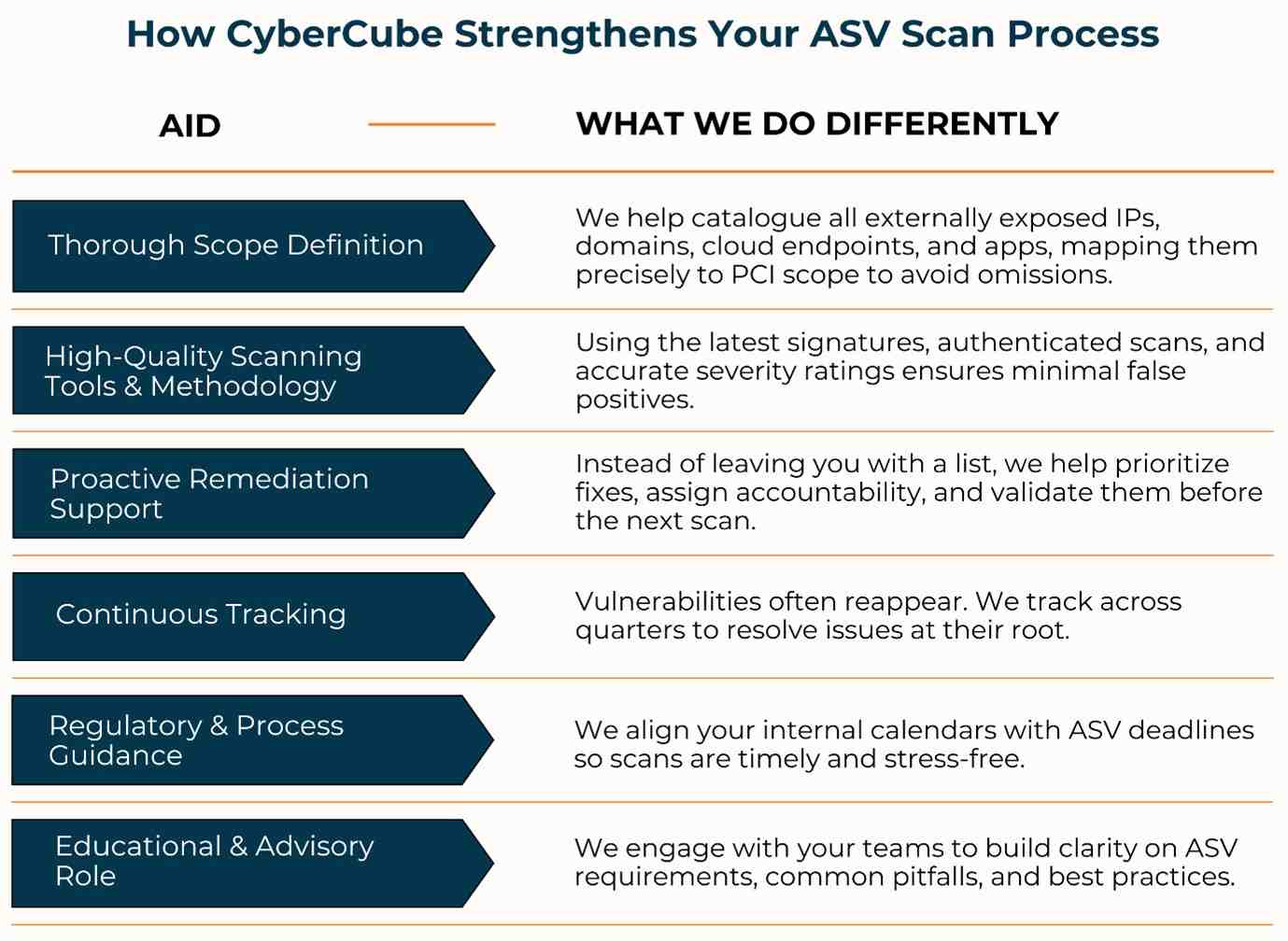
How CyberCube Helps You Not Just Pass, But Be in Control
What sets CyberCube apart is not just running scans but integrating them into your risk reduction and compliance lifecycle.
ASV Scan Cost: What to Expect
For many organizations, one of the first questions is, “How much will an ASV scan cost?” The answer depends on a few variables:
- Number of IP addresses or domains — more assets in scope mean higher scanning costs.
- Engagement type — one-time scans typically cost more per instance compared to annual packages.
- Support levels — some vendors provide just the report, while others (like CyberCube) add advisory and remediation assistance.
- Environment complexity — hybrid, multi-cloud, or legacy-heavy infrastructures often require additional scanning effort.
On average, organizations can expect ASV scan pricing to range from $200 to $1,000 per scan, with annual packages offering better value for recurring quarterly requirements.
Disclaimer: These figures are indicative. Actual costs vary significantly by vendor, scope, and service level. Always request a tailored quote based on your specific environment.
Get a Fixed-Scope Quote
Transparent pricing based on your asset count and environment. No surprises.
Best Practices for Consistently Passing ASV Scans
Companies that pass scans reliably approach compliance as part of the everyday security workflow—not a quarterly scramble. Here’s what works, based on experience inside real organizations:
- Keep Your Inventory Up-To-Date: You can’t secure what you don’t know about. Make asset discovery an ongoing process—not something you only do when the next scan is due. Automate it if you can. Include not just traditional servers, but cloud workloads, APIs, and anything else facing the internet.
- Patch Early and Often: Don’t wait for a scan to flag outdated software. Build a regular patch cycle into your team’s culture. Prioritize high-severity vulnerabilities, and make sure someone “owns” the job of getting patches deployed well before your scan window.
- Harden by Default: Every new server or application goes live with hardened, secure settings. Use benchmarks like those from the Center for Internet Security (CIS). Turn off unused services, enforce strong encryption, and change default credentials on everything.
- Pre-Scan Internally: Want a scan day with no surprises? Run internal vulnerability assessments regularly between official scans. Many organizations schedule weekly or monthly scans using the same tools ASVs do. This way, the quarterly scan becomes a formality, not a crisis.
- Assign Clear Roles & Track Remediation: Give someone (or a small team) clear ownership of the ASV scan process. Track remediation steps, document vulnerabilities found and fixed, and keep an audit trail for every step. This not only helps with compliance but prepares you for smoother audits in the future.
Making ASV Scans an Advantage
If you treat ASV scans as just another compliance box to check, you’re missing out. These scans are actually a great reality check—a way to stay honest about the health of your organization’s defenses.
Shift your mindset: Let passing your ASV scan be the result of a continuous, everyday process. The payoff? Twofold:
- No audit panic: You have confidence that your reports will be clean and ready for submission when it counts.
- Better real-world security: Fixing vulnerabilities at their foundation means your actual risk—not just your compliance status—goes down.
Setbacks are normal, but they don’t have to become the status quo. With a little discipline, clear roles, and the right tools in your corner, failed scans can become a problem of the past. Take control by keeping tabs on your assets, patching proactively, and making compliance part of your culture—not just a deadline.
Security is a journey, and passing your ASV scan is just one of the milestones. Use every scan as an opportunity to strengthen your defenses and build trust—with your customers, your partners, and within your team.
Ready for a smooth ASV pass—every quarter?
We’ll align scope, harden configs, and coordinate scanning so compliance becomes predictable.
Talk to CyberCube