
Cybersecurity never sits still, and neither do those looking to exploit its vulnerabilities. Over the past year, a new player has entered the scene—one with a strange name and a very real threat: the Gayfemboy malware. If you work in IT or security, you have probably heard some chatter about this unusual yet very real malware variant. What started as a quirky variation of the well-known Mirai botnet is now actively disrupting businesses around the world by using advanced tactics and demonstrating long “hide-and-seek” persistence.
The Gayfemboy malware is not merely a nuisance—it is turning everyday devices into weapons for cybercriminals, executing powerful DDoS attacks, and creating operational headaches across continents. Below is what you need to know—and, more importantly, how to defend your organisation from becoming the next target.
Threat Briefing Call (15–20 mins)
Validate indicators, scope likely exposure, and prioritise near-term hardening steps.
What Is Gayfemboy Malware?
At its core, Gayfemboy malware is a cleverly built evolution of the Mirai botnet. If Mirai sounds familiar, that’s because it made headlines for knocking huge chunks of the internet offline back in 2016. Gayfemboy, discovered in early 2024, picks up where Mirai left off but with a bag of tricks that makes it even harder to contain.
So, what does it do exactly? Gayfemboy looks for unprotected IoT devices, routers, and computers—think security cameras, office printers, or even smart thermostats. Once inside, it transforms these gadgets into a “botnet”—basically, a zombie army that hackers can remotely control. Then, with the press of a button, all these devices bombard selected websites with junk traffic, overloading servers and causing outages in what’s called a distributed denial of service (DDoS) attack.
Unlike some hackers who go straight for your bank account or sensitive data, the operators behind Gayfemboy are playing a bigger game: control enough devices, and you can take websites or services offline at will. That level of power can be sold, rented, or used for blackmail—making DDoS-for-hire a growing business in the cybercriminal underworld.
Tracing the Evolution: From Mirai to Gayfemboy
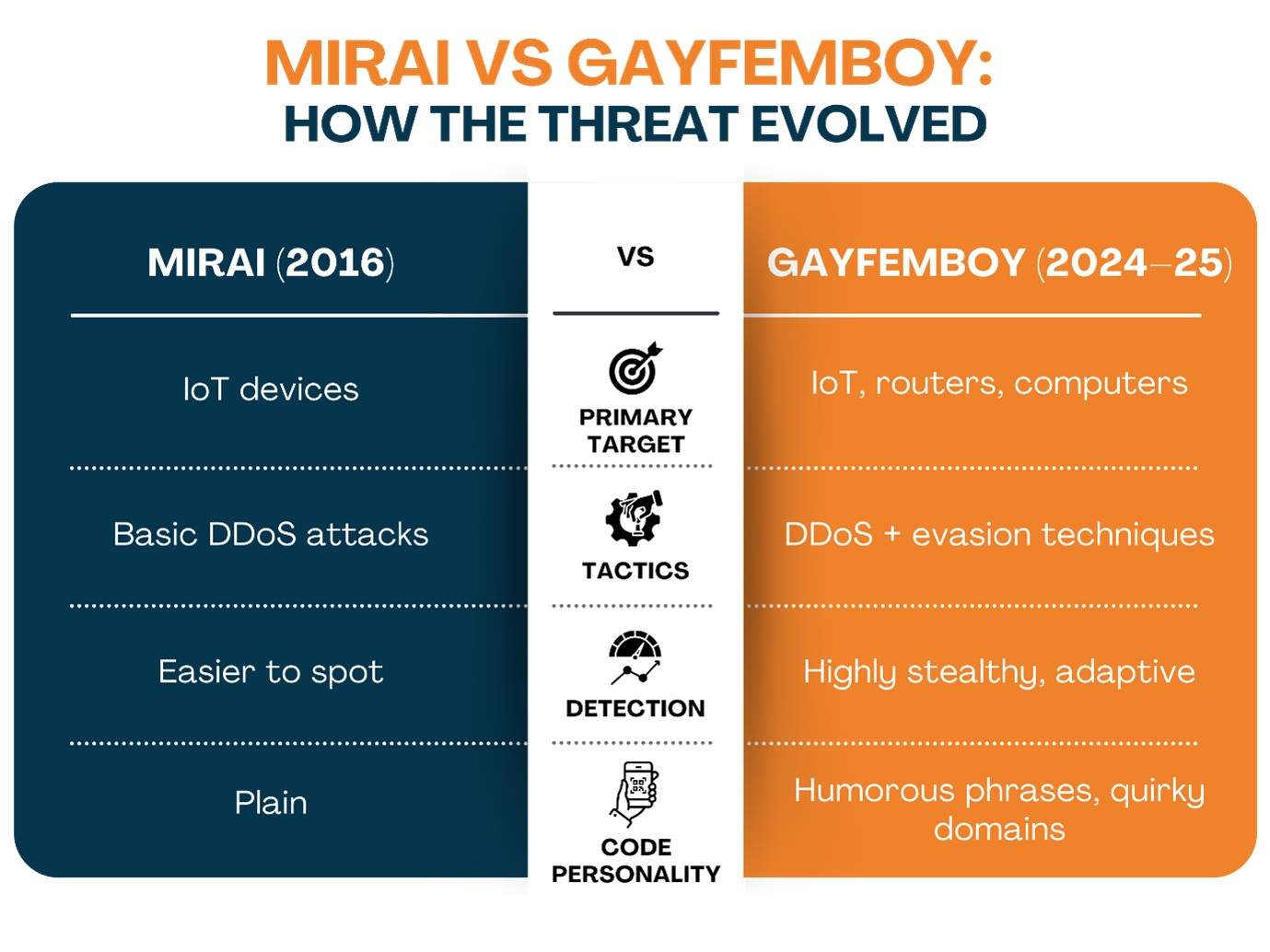
It might be tempting to dismiss Gayfemboy as just another malware offshoot, but that would be a mistake. The malware draws inspiration from Mirai, yet raises the stakes with a host of new features and a personality to match.
First noticed in February 2024, Gayfemboy quickly proved it wasn’t a fluke. By the start of 2025, it had helped pull off hundreds of DDoS attacks. A spike in attacks over the summer, reported by experts at Fortinet.
The genius (or madness) behind Gayfemboy is its ability to hang around undetected. It borrows moves from older botnets but keeps evolving, finding new ways to outmaneuver antivirus software and evade security teams. Think of it as a game of chess—every time the defense learns a move, Gayfemboy adds two more.
Where Has the Damage Been Done? Countries and Industries at Risk
Gayfemboy isn’t picky about where it spreads. Attacks have been documented in Brazil, France, Germany, Israel, Mexico, Switzerland, the United States, and Vietnam, making it a global headache for anyone depending on the internet to get their work done.
Hackers behind Gayfemboy seem particularly interested in cryptocurrency mining operations. Many attacks in recent months have targeted systems running XMRig, a popular tool for mining digital coins. But they haven’t stopped there. Manufacturing, finance, healthcare, and the tech industry have all reported hits. If your business relies on connected devices—or if it’s a tempting target for cyber attackers—chances are, Gayfemboy is on the lookout.
What's striking is that the attackers aren’t after any one industry—they’re after opportunity. The more devices they control, the more chaos they can unleash.
What Makes Gayfemboy Different: The Code with Character
Most malware tries to blend in, but Gayfemboy stands out. Its code isn’t just technically savvy—it’s got an attitude. When executed, it flashes quirky phrases like “twinks :3” on infected systems. It even makes use of the hilarious password "meowmeow" in order to trigger secret backdoors, and the command servers have domain names such as "i-kiss-boys," "furry-femboys," and "twinkfinder."
It's easy to be entertained by the details, but don't let it distract you. Underneath the jokes is a highly effective program. These humorous names may help security experts track viruses and identify new outbreaks, but they also demonstrate the creators of the malware are bold and have great technical web skills.
Underneath, Gayfemboy has some serious anti-detection technology. It can change file names on the fly, hide under inactive scripts when it senses a scan, and even mimic normal system behaviour if it thinks someone’s watching. It’s like a chameleon with a sense of humour—one that you don’t want anywhere near your network.
How Does Gayfemboy Avoid Getting Caught?
Security teams and antivirus programs have their work cut out for them with Gayfemboy. Fortinet flagged the malware as high-risk for good reason—it keeps finding new ways to sidestep traditional detection.
One minute, the malware is hiding under a random process name. The next, it’s hibernating, doing nothing to avoid drawing attention. It springs back to life instantly if it receives instructions from its controller. And when an IT team comes in, it adapts yet again, always one move ahead.
If your company is still relying on standard, signature-based antivirus software, be careful. Gayfemboy is an expert in blending in, and this means that infections can remain in a host for months without triggering a single alarm.
The Cybersecurity Challenge: Why Is This Such a Big Deal?
Gayfemboy’s success puts a spotlight on some uncomfortable truths about modern cybersecurity. For starters, relying solely on outdated security practices is risky—especially as hackers get smarter and bolder.
Many of Gayfemboy’s favourite targets are basic IoT devices and routers, partly because these are often neglected when it comes to security updates. Has your organization changed the default password on every smart gadget? When was the last time that old printer got a firmware update? If you’re not sure, you’re definitely not alone.
International attacks make fighting back even harder. Different countries have different laws and levels of readiness. Coordinating a response gets tricky, especially when hackers move fast and the scope is global.
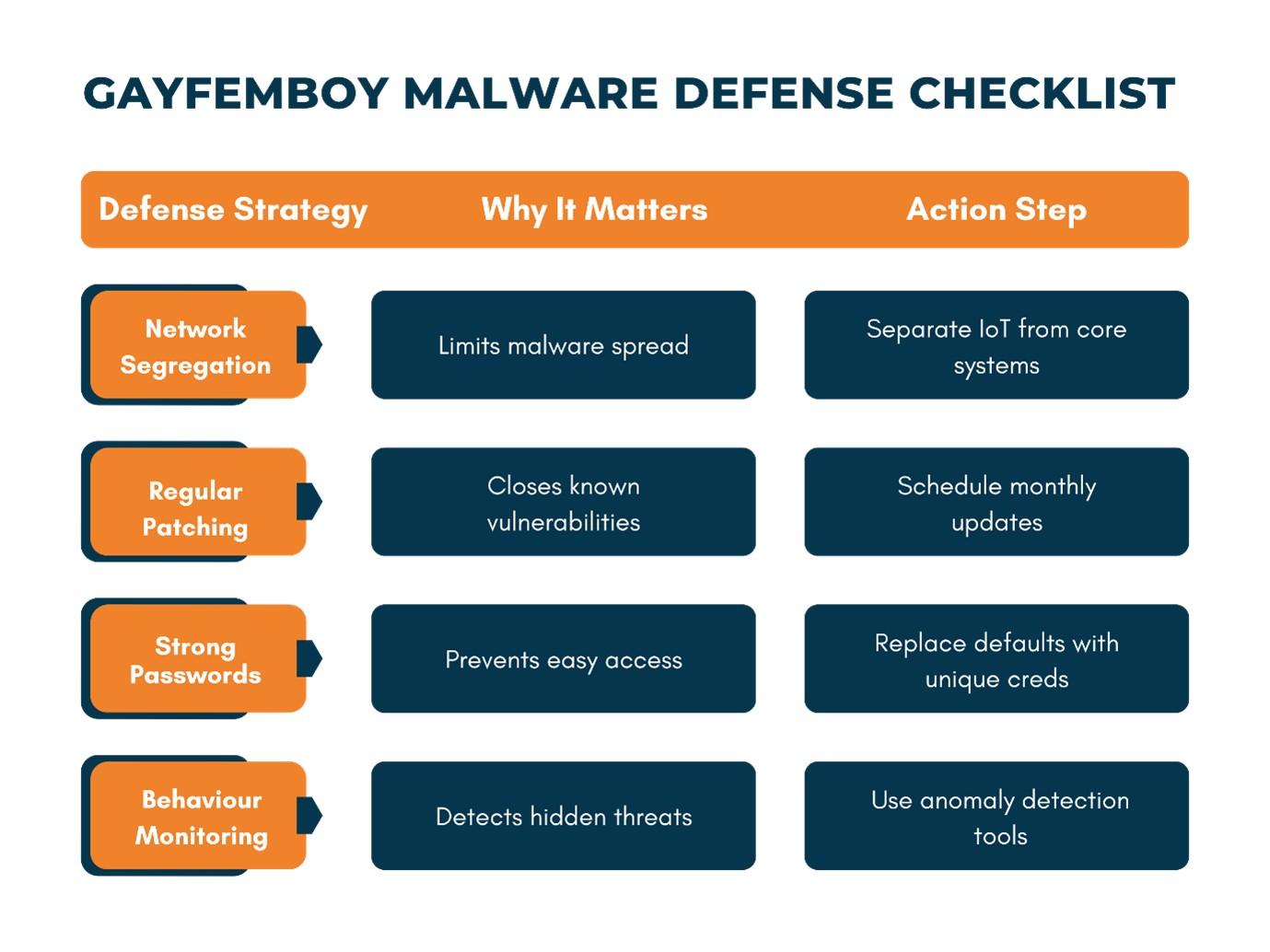
How to Defend Your Organization Against Gayfemboy Malware
Beating malware like Gayfemboy takes a layered approach—a “castle wall” of defenses rather than relying on one single moat. Here are some actionable steps any organization can start with:
DDoS & IoT Resilience Workshop
Model attack paths, validate controls, and produce a 60-day hardening plan with quick wins.
The Road Ahead: Staying Safe in an Evolving Threat Landscape
Gayfemboy offers a glimpse of what the future of cyber threats looks like—creative, persistent, and obviously not easily deceived. With every adaptation malware writers make, we need to adapt, including our methods as defenders. Threat intelligence and a proactive attitude are critical in risk and threat mitigation plan for any organization that is embracement of their cybersecurity and information security initiatives.
For organizations to get or stay ahead, they should research and implement smarter detection products, develop clear response plans for when (not if) the trouble begins, and follow helpful new resources that discuss the new threats coming across the web.
Gayfemboy should serve as a wake-up call that even the most ridiculous-seeming malware might be effective at causing chaos. We are all on a digital battlefield, but only those who see cyber security as a journey will find a way forward amongst the chaos.
As long as you remain vigilant and ensure your security stays current, you'll be protecting your organization and ensuring that malware like Gayfemboy has the final laugh. Keep your staff educated and bait every device as a potential target—recent attacks show this might not just be a fishing expedition.
Need help triaging indicators or hardening edge assets?
We’ll review telemetry, prioritise fixes, and align providers for DDoS protection—fast.
Talk to CyberCube