
The speedy transition to cloud-native development has changed the containers to the engine of modern applications. The efficiency and portability of containers allow organizations to innovate at a faster pace than previously possible. However, with that speed the attack surface has grown larger and more complex. By the beginning of 2026, protecting containerized or orchestrated environments is no longer a mastery of a technical audience, but instead, a need in business. An inadequate container security posture can compromise sensitive data, take services offline, and be detrimental to your organization’s brand or reputation.
We will discuss the top threats, considerations that you can use to implement best practice, and top tools that can be used to automate and improve your security posture. By the end, you will have a simple guide to keep your applications secure from development to production.
The Importance of Container Security
Containers provide a way to bundle an application with all of its dependencies into a self-sufficient unit that can execute anywhere. This utility has led to rapid adoption. However, containers are also inherently complicated, and their interconnectedness leads to unique security vulnerabilities that legacy methodologies will not protect against.
By 2026, there is a high chance for even greater risk for a few reasons:
- Scale and Complexity: Organizations now operate thousands of containers in service with multiple clouds and on-premises workloads. A single vulnerable base image, deployed across the landscape, could potentially spread throughout your entire infrastructure within minutes, becoming nearly impossible to track manually.
- Advanced Attack Vectors: Threat actors are targeting containerized environments and using advanced tooling against common issues like unsecured APIs or exposed or unsecured Kubernetes dashboards or even hard-coded credentials stored inside the container images.
- The Software Supply Chain is the Best Target: Applications are built using a combination of first-party code and third-party libraries. A compromised open-source package, or a compromised base image, can infect the application directly in the software supply chain.
- Growing Regulatory Compliance Pressure: Compliance frameworks like PCI DSS 4.0, NIST 800-190, and ISO 27001 now come with requirements for container security. Organizations must be able to demonstrate sufficient controls for vulnerability management, runtime protection, and network segmentation to avoid being in violation.
Unless you have a dedicated strategy, you are literally leaving the doors open to your most sensitive applications. Strong container security provides the perspective and control to address and manage those risks while keeping your infrastructure agile and resilient.
The Growing Container Ecosystem
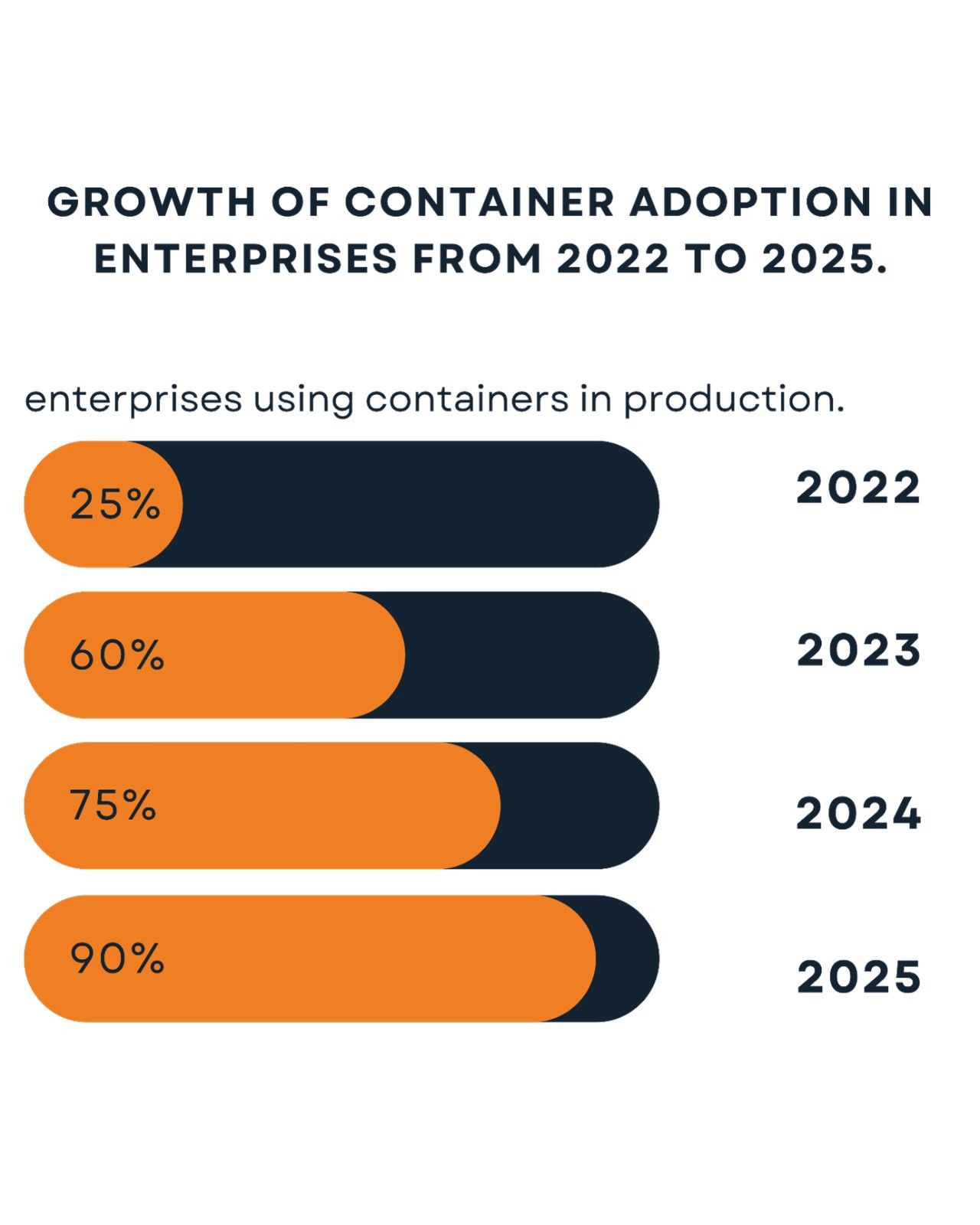
Source: Industry Projections (e.g., Gartner, CNCF)
Container Security's Key Threats
To build a robust defense, the first step is to understand your adversary. Attackers employ various types of approaches to take advantage of vulnerabilities in containerized environments. Here are the threats you need to be aware of:
- Vulnerable and Malicious Container Images: Many development teams pull base images from repositories like Docker Hub without validating them for known vulnerabilities. These images can include outdated software with known vulnerabilities, or worse yet, malicious code that is going to inject malware, crypto-mining programs, and potentially backdoors within the image. If you build an application on a compromised base, you get all the risks associated with that base application as well.
- Misconfigured Permissions and Access Controls: During the rush to deploy applications, the concept of least privilege is often forgotten. Archaic RBAC settings in orchestrators such as Kubernetes can provide an attacker, who gains access to a single container, access to the entire cluster. When an attacker has access to a cluster, they can move laterally, elevate their privileges, and gain access to sensitive resources.
- Container Escapes: A container escape is a scenario where a process running inside a container breaks out and gains access to the underlying host operating system. This is a critical breach, as it gives the attacker control over the host and all other containers running on it. While rare, escapes are often caused by severe kernel vulnerabilities or misconfigurations in the container runtime.
- Unsafe Secrets: Embedding secrets such as API keys, database passwords, and authentication tokens as part of a container image or through environment variables is a common but insecure practice. If an image becomes compromised or an attacker gets access to a running container, the secrets stored there become available and give the attacker an easy way to get access to your most valued data and services as a result.
- Poor Network Segmentation: By default, a Kubernetes cluster allows any containers to communicate with other containers most of the time. This creates a flat network design which permits attackers to quickly pivotable to targets that are of value (e.g., a database or payment processing service) if they compromise a less valuable non-production container. Very low or no micro segmentation in Kubernetes clusters removes internal barriers that might limit the damage from a compromise.
Best Practices to Secure Your Containers
To protect against these threats, you need a proactive and layered approach to security, and integrating security into each phase of the application lifecycle by practicing DevSecOps is your best option.
1. Securing Your Build: Shift-Left Security
Security should not be added at the end of your process; security should be a part of your CI/CD pipeline.
- Only Use Trusted Images: Use and maintain an internal registry of approved, hardened base images and ensure developers cannot pull images from unknown, public registries.
- Scan Images for Vulnerabilities: Scan every container image with an automated scanner for known vulnerabilities against any OS packages and libraries your applications rely on. Every build containing critical or high severity issues should fail.
- Produce a Software Bill of Materials (SBOM): An SBOM is simply a list of every component of all of your software. It provides you visibility, and the ability to comprehend dependencies and react quickly to vulnerabilities in the applications you have once they are disclosed.
2. Secure the Deployment: Policy and Configuration
Before a container is live, the deployment configuration must be secure.
- Enforce Least Privilege: Always configure least privilege at the Kubernetes RBAC (Role-Based Access Control) policy level to give users and service accounts only what they need to know. There should never be a reason to use default or cluster-admin type roles.
- Implement Security Contexts: Make use of security contexts to provide your pods and containers with only the permissions that they need for them to function. For example, use non-root containers and configure a read-only root filesystem.
- Automate Policy Governance: Leverage a policy-as-code tool like OPA/Gatekeeper or Kyverno to programmatically governance policies into the admission controller. For example, if the admission controller is configured to block the deployment of a container with root permission it should trigger that policy for any containers or pods trying to deploy with such permissions.
3. Secure the Runtime: Real-Time Protection
While it’s best practice to proactively secure your applications, you also need to be ready to detect and respond to a threat while it’s occurring in real-time.
- Monitor Runtime Behaviour: Deploy a runtime security tool that is able to identify anomalous behaviour in real-time. An example of anomalous behaviour is an application initiating a connection to an unexpected external IP address. It could also include a process accessing files or executing processes when the behaviour is out of the norm. These are examples of availability attacks, and they are your last line of defense against zero-day exploits.
- Execute Network Microsegmentation: Provide extremely granular rules in the definition of what traffic you will permit between each pod using Kubernetes network policies. An example could be the default everything denied, with only the explicit requirements for the application to function being allowed.
- Threat Detection and Response: The detection of compromise is nothing more than a remediation tool to continue the detection of anything searched for. When you have risk systems monitoring for threat and identify a threat, you will need to manage the trauma of a plan for remediating accidents, such as, isolating, killing, or otherwise restricting the vulnerability container to limit the impact of the attack, at a breach events.
Embedding security throughout your development workflows, enforcing access controls, and monitoring your runtime can build a security status that is both strong and flexible. At a minimum, prioritize securing your images, shutting down permissions, and visibility into what is going on in your clusters. From there, you can mature to advanced runtime defense and automated policy enforcement.
Don’t wait until you have a breach to make container security a priority. Start immediately.
Secure Your Containers with CyberCube
CyberCube helps enterprises design and deploy container security strategies across Kubernetes, Docker, and hybrid-cloud environments. Get a full container security assessment today.
Talk to CyberCube