
Every year, the cybersecurity world waits to see what will land on the OWASP Top 10 list—the definitive ranking of the biggest risks to applications. And year after year, one category refuses to budge from the top: security misconfigurations. It’s a stubborn problem, but also an avoidable one if you know where to look.
Whether you’re a seasoned developer, a business leader, or you just want to know how safe your organization’s data really is, this blog will tell you why security misconfigurations remain one of the top 10 threats, and more importantly, what you can do to spot and fix them before trouble starts.
Misconfiguration Review Call (20 mins)
Validate your OWASP posture, identify weak points, and get a prioritized fix roadmap.
So, What Is a Security Misconfiguration?
At its core, a security misconfiguration is - a system or application that has been configured without the proper security.
Think of it like moving into a new apartment and forgetting to change the locks, everything was fine, you left the windows wide open, and ensured to put your spare key under the doormat. On the surface, there was nothing wrong - but if someone recognized your apartment complex and was looking for a way in - it would take just one person to cause some trouble.
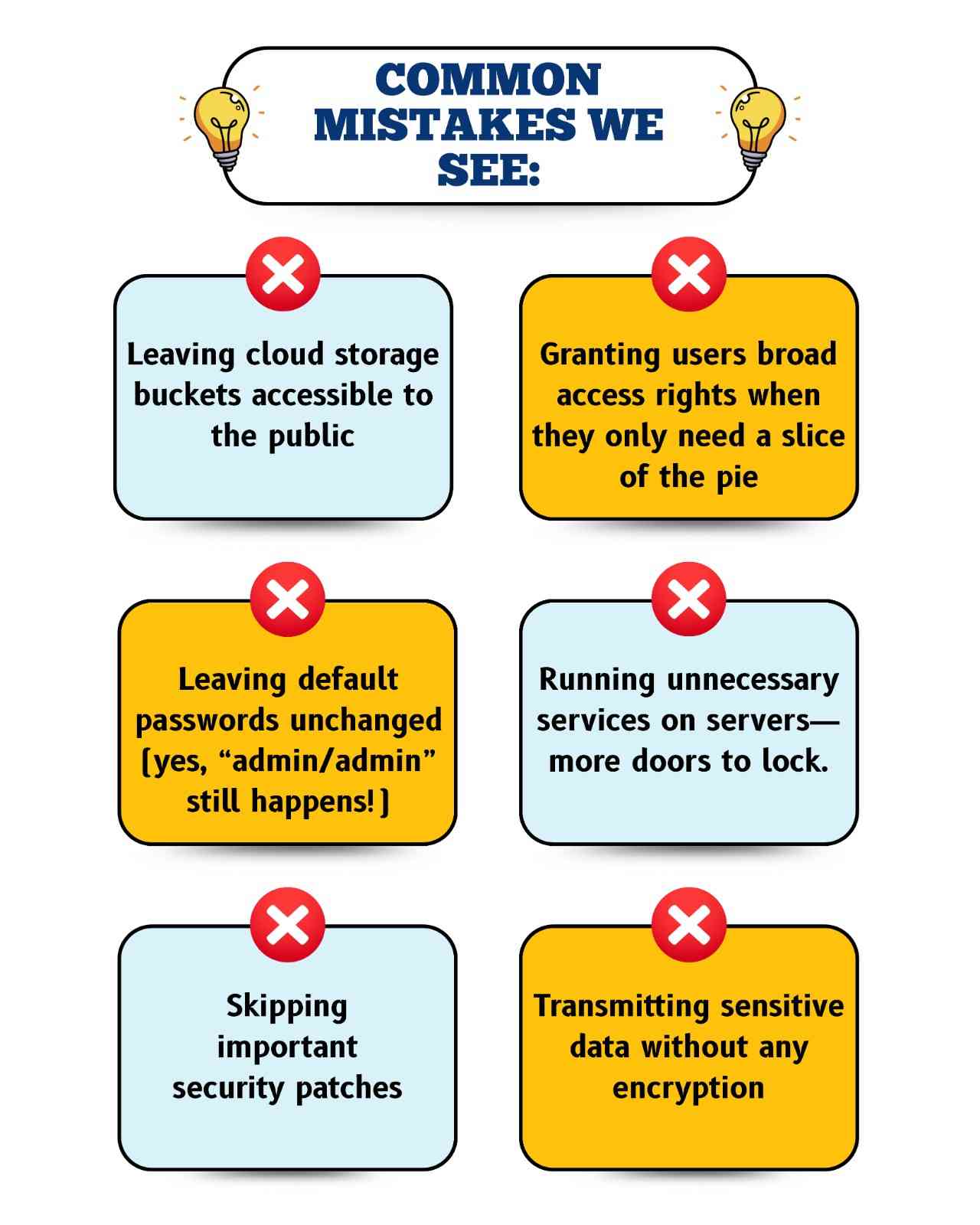
Here are a few of the most common mistakes we see:
Unlike a malware infection (which usually sends up red flags), misconfigurations tend to lurk quietly in the background—sometimes for years—waiting for an attacker to stumble upon them.
Why Are We Still Struggling with Misconfigurations?
Let’s be honest: technology can be complicated, and teams are moving faster than ever. Cloud adoption, DevOps, and rapid digital transformation create endless opportunities… and just as many chances to slip up.
Here’s why these mistakes keep happening:
- Everything's Getting More Complex:
Our apps aren’t simple anymore. They’re built out of databases, APIs, microservices, and cloud stuff—all talking to each other and all needing their own security settings. The more moving parts, the easier it is to overlook something.
- Speed Wins—But at What Cost?
Businesses are under pressure to innovate quickly. That often means new features roll out before anyone double-checks the settings, or security get treated as an afterthought.
- Not Everyone Is a Security Pro:
IT teams are busy and skilled, but not everyone is a security expert. Sometimes it’s easy to focus on performance and forget to review permissions or encryption settings.
- Defaults Aren’t Your Friend:
Out-of-the-box, many tools have an emphasis on the user experience and broad compatibility.
Real Stories, Real Impact
These aren’t just “what-ifs.” They’re happening all the time.
Take the Capital One breach in 2019—over 100 million customer records were exposed because a web application firewall wasn’t set up correctly. Or the Equifax breach in 2017: it wasn’t an ingenious hacking plot—it was an unpatched server and some missed configuration steps that allowed attackers in.
Both stories are scary reminders that even the biggest companies can be undone by small slips in security.
Regulators notice when companies suffer steep fines, lawsuits, bad press, and a loss of trust from customers. It can take years—and a lot of money—to rebuild a reputation after just one misconfiguration.
Let's look at how cloud misconfigurations make things more complicated.
Moving to the cloud adds speed and scaling, yet simultaneously, it adds another layer of risk. As opposed to traditional networking, cloud services have a shared responsibility; you are responsible for securing your configuration and the cloud provider is responsible for securing hardware and core infrastructure. It is like renting a car, you are still required to wear your seatbelt and drive safely.
Watch out for these common cloud misconfigurations:
Storage like Amazon S3 or Azure blobs set to “public”—anyone with a link can peek inside
Firewall rules (Network Security Groups) left too open—inviting unwanted visitors
User accounts and service roles with way more access than needed
Forgetting to switch on encryption for sensitive data
Not enabling proper logging—so you’re in the dark if something does go wrong
With cloud, it’s easy to scale up fast—one tiny error in a deployment template and dozens of insecure resources appear at once.
Cloud Misconfiguration Review
Run a 1-hour session to identify exposed storage, misconfigured firewalls, and weak identity policies.
Catching Misconfigurations Before They Cause Trouble
Spotting (and stopping) misconfigurations is possible, but it means getting proactive. Here’s how you can build strong habits that payoff:
- Embrace Automated Scanning
- Infrastructure-as-Code Scanners (like Checkov or Terrascan): These scan your setup scripts before you hit “deploy.”
- Runtime Configuration Monitors: These check running systems for deviations from your intended settings.
- Cloud Security Posture Management (CSPM): Platforms that constantly monitor your cloud environments for red flags.
Relying on memory or checklists doesn’t cut it. Modern security teams use automated tools that compare your actual settings with known good (secure) baselines and flag anything out of place. Some tools worth exploring:
- Integrate Testing into Development
- Static Analysis: Scanning code and configuration files as they’re written to highlight risks early.
- Dynamic and Interactive Testing: Watching how live systems behave to spot real-world issues you might’ve missed during setup.
Security shouldn’t be bolted on at the end—it should be woven into the whole development cycle. That means:
- Make Smart Processes a Habit
- Standardize Configuration Templates: Utilize pre-vetted templates for servers and cloud resources so you won't have to reinvent the wheel (or risk missing best practices).
- Enforce Peer Reviews: Don’t let one person make all the calls. Fresh eyes catch simple mistakes.
- Automate Compliance Gates: Set up your deployment pipeline so systems can’t go live unless they pass key security checks.
Some practical ways to minimize mistakes:
Building Security into Your Culture
Tools are helpful, but a culture is what holds your team together for the long haul.
Training Everyone: Be sure to make good security training a regular, bite-sized piece of job training that affects not only the security team, but also developers, testers, and business folks.
Make Responsibilities Clear: Who owns which parts of the system? If it is not clear, no one truly owns it—and things fall through the cracks.
Learn and Share: When you do find a misconfiguration, do not just fix it quietly, perform a post-mortem.
Ready to Act? Don’t Wait
If there’s one takeaway here, it’s this: security misconfigurations remain at the top of the OWASP Top 10 because fixing them takes more than tools—it’s about habits, teamwork, and a willingness to ask hard questions about how things are set up.
Start today. Do a quick audit of your critical systems. Ask your developers if they use standardized templates or automated tools to catch drift. Bring your teams together to talk honestly about security. The goal isn’t a perfect score—it’s a culture where mistakes are found and fixed before attackers can find them.
There’s no shame in having a misconfiguration. The only mistake is ignoring the risk and hoping for the best.
Remember: attackers are always looking for the unlocked door. Make your systems the ones that are always locked up tight.
Want help reviewing your cloud or application security? Our team can help you find and fix misconfigurations—before they become tomorrow’s headline. Reach out today for a Cloud Security Review or Application Security Testing to see how you stack up.
Need help preventing configuration drift?
Get a comprehensive review of your app and cloud configurations against OWASP benchmarks.
Talk to CyberCube