
In 2026, AI-Driven Threat Exposure Management will be a New Approach to Mitigating Cyber Risk
The cybersecurity teams are becoming overloaded with the number of alerts generated by their various dashboards and different disconnected tools that they use to protect against cyber-attacks. There are many different types of alerts generated by vulnerability scanners, thousands of vulnerabilities listed in their Cloud Security Platforms, and constant alerts from Pentesting per Report(s) identifying exploitable weaknesses. Yet there are still many data breaches occurring throughout the world.
Cybersecurity Teams are Not Lacking Data; They Are Lacking Context and Prioritisations.
Threat Exposure Management (TEM) is emerging as one of the Hot Cybersecurity Trends of 2026 which is actively being searched for by many organisations, thus creating a large Demand for SEO driven visibility.
In this blog, we’ll break down what Threat Exposure Management really is, how AI is changing the way exposure is identified and reduced, and why TEM is quickly replacing traditional vulnerability management approaches.
Want a TEM-style Exposure Snapshot?
We’ll map your exposed assets, likely attack paths, and the fixes that reduce real risk first.
What Is Threat Exposure Management (TEM)?
Threat Exposure Management is a continuous, risk-focused approach to identifying, prioritizing, and reducing an organization’s real-world attack surface.
Unlike traditional security practices that focus on isolated findings, TEM answers a more important question:
Which security weaknesses can actually be exploited right now—and how likely is that impact?
TEM brings together signals from multiple security domains, including:
- External attack surface discovery
- Vulnerability intelligence
- Cloud and identity exposure
- Configuration weaknesses
- Threat actor activity and exploit trends
Instead of treating all issues as equal, TEM connects them into attack paths that mirror how real attackers operate.
Why Traditional Vulnerability Management Is No Longer Enough
For years, vulnerability management has been the backbone of defensive security. But modern environments have changed.
Key limitations of traditional approaches:
- Volume without clarity: Thousands of CVEs, little guidance on what matters
- Static severity scores: CVSS doesn’t reflect real exploitability
- Siloed tools: Cloud, endpoint, network, and identity risks viewed separately
- Reactive workflows: Fixing issues after alerts instead of preventing attacks
Attackers don’t exploit vulnerabilities in isolation. They chain together weaknesses across systems. TEM is designed specifically to address this gap.
Cut Through Alert Fatigue
Prioritize exposures based on exploitability and impact, not volume.
How AI Powers Modern Threat Exposure Management
AI is not just an enhancement—it is foundational to effective TEM.
- Intelligent Asset Discovery
AI-driven engines continuously map internet-facing assets, shadow IT, APIs, cloud workloads, and third-party exposures. This ensures organizations are defending what actually exists, not what they think exists. - Contextual Risk Scoring
Instead of relying only on severity scores, AI evaluates:- Is an exploit publicly available?
- Is the asset exposed externally?
- Is it linked to sensitive data or critical systems?
- Has this attack path been observed in the wild?
- Attack Path Simulation
Machine learning models analyze how attackers could move laterally—from a low-risk misconfiguration to a high-impact breach. Security teams can visualize the shortest path to compromise and break it early. - Continuous Threat Intelligence Learning
By correlating exposure data with active Threat Intelligence (TI), techniques/exploits used by cyber criminals, and the attacks they are engaged in (e.g. Cyber-Breach attacks) AI keeps the prioritization to align with what is happening at that moment.
Traditional Security vs Threat Exposure Management
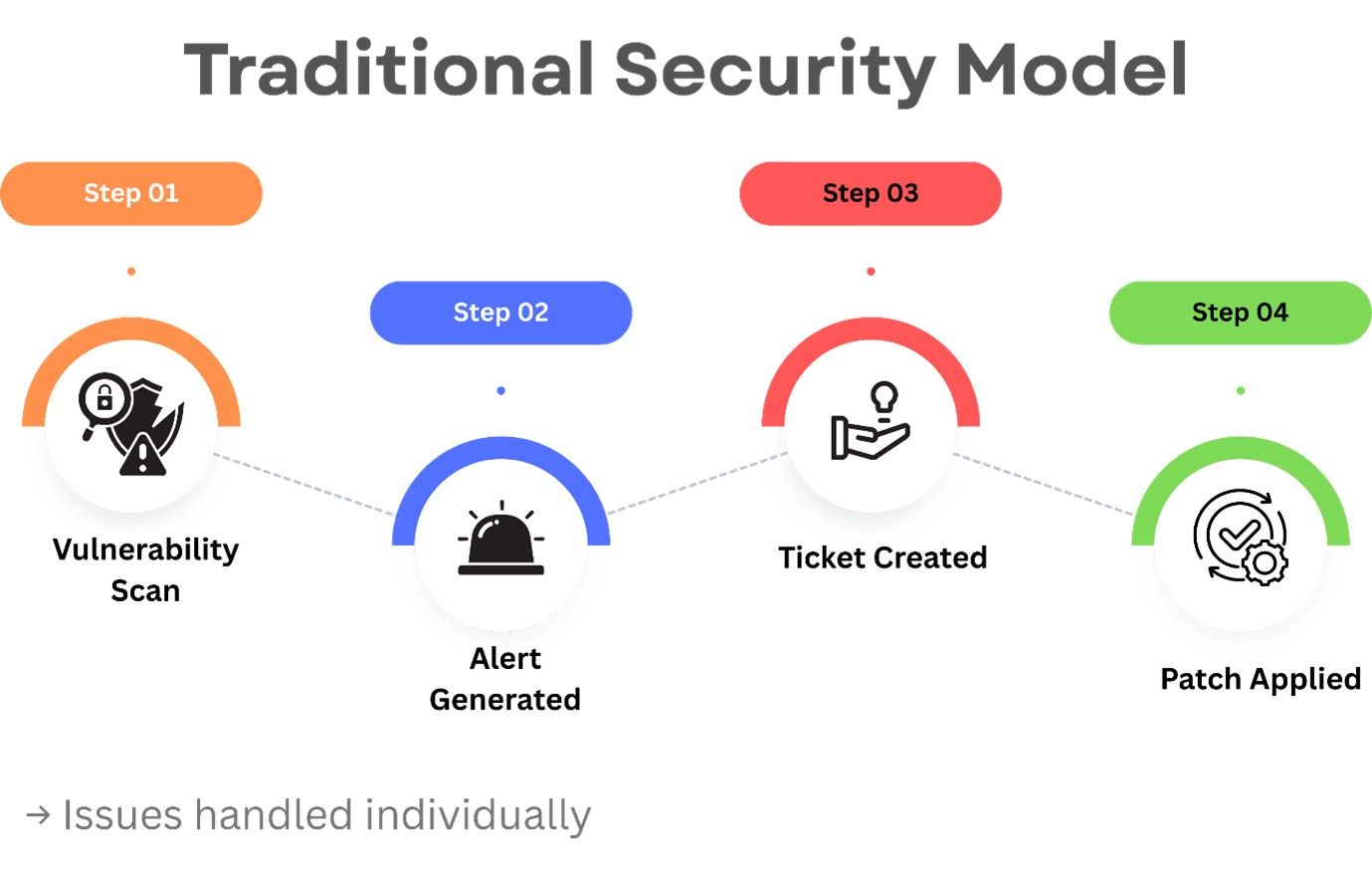
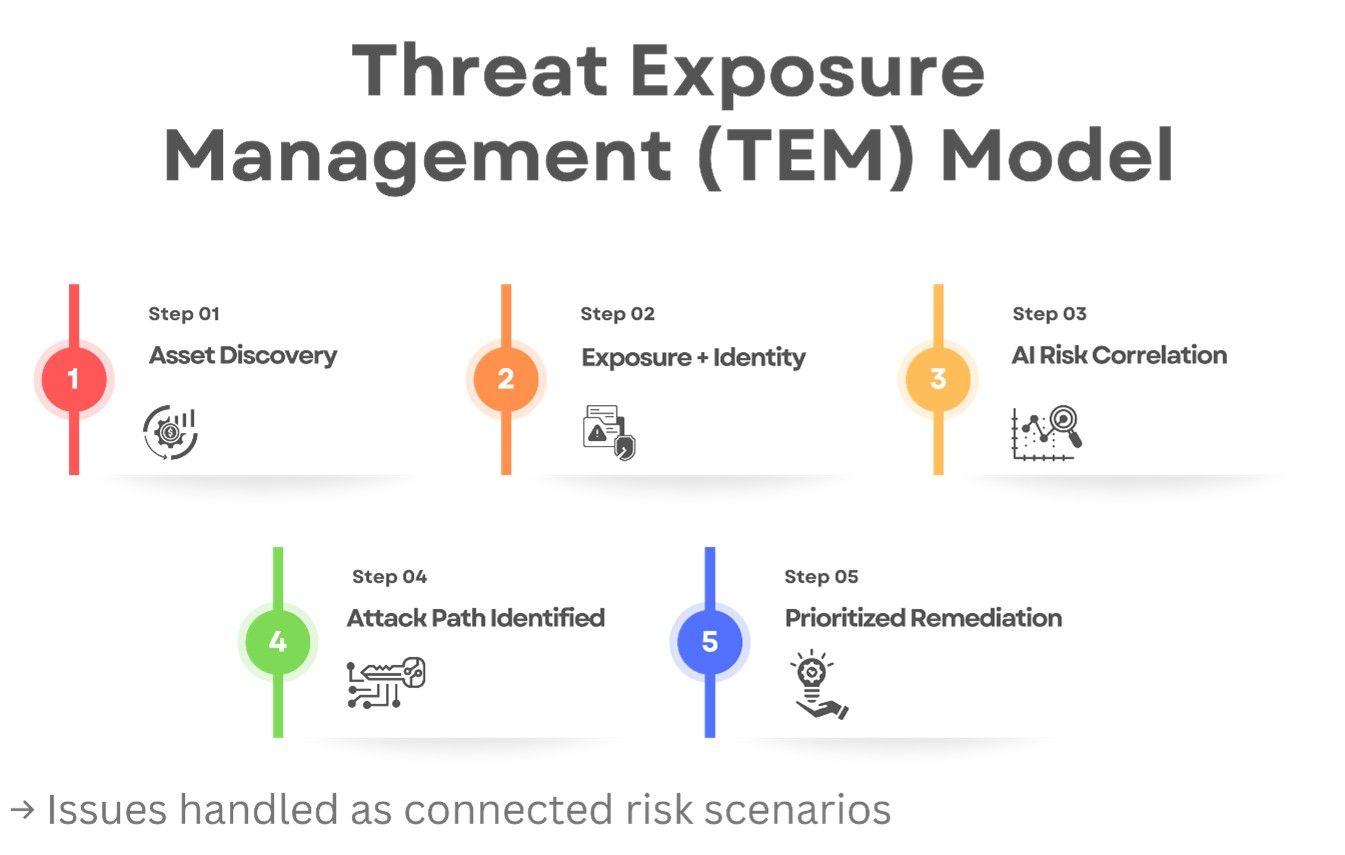
The following elements are essential for an effective Threat Exposure Management Programme
- External Attack Surface Management (EASM): EASM helps identify all external facing assets of an organisation (exposure for attackers), including domains, subdomains, Cloud-based services, and often forgotten infrastructure.
- Vulnerability and Weakness Intelligence (VWI): VWI gathers data on the existence of vulnerabilities and weaknesses in an organisation and correlates that information with how readily available exploits and/or attacker interest exists for those vulnerabilities.
- Identity and Access Exposure: Identity and Access Exposure is exposed by showing the risk (that attackers would exploit) associated with excessive access rights, stale accounts, and privileged escalation paths.
- Cloud/Configuration Risk: Cloud/Configuration Risk is detected through the identification of misconfigured services within an organisation's Cloud Infrastructure, SaaS Infrastructure, or Hybrid solution that widen the attackable surface for potential threat actors.
- Remediation Based on Risk: Remediation activities should concentrate on what poses the greatest risk and directly lowers the chances of successful attacks rather than solely on the number of "alerts."
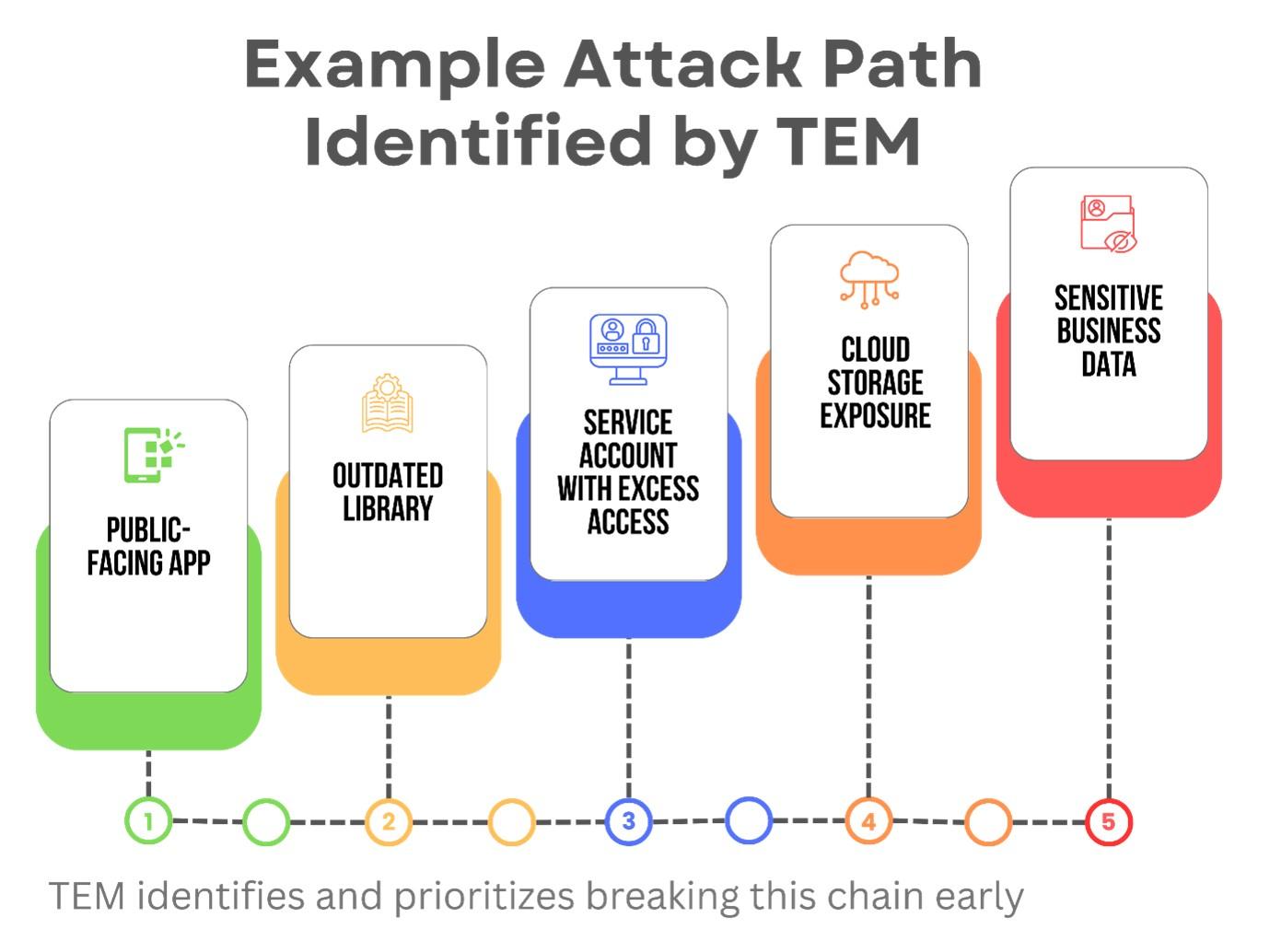
See Your Real Attack Paths
We’ll show how exposures chain together and what breaks the path fastest.
Business Benefits of Threat Exposure Management
- Reduced Noise, Better Focus: Security teams spend less time chasing low-impact findings and more time fixing what truly reduces risk.
- Faster Decision-Making: Leadership gains a clear, risk-based view of exposure instead of fragmented technical reports.
- Proactive Defense: TEM enables teams to disrupt attack paths before exploitation occurs.
- Better ROI on Security Tools: By correlating existing security investments, TEM maximizes value without adding unnecessary complexity.
Why Threat Exposure Management Is a High-Intent Search Topic
Organizations searching for Threat Exposure Management are typically:
- Struggling with alert fatigue
- Managing complex cloud and hybrid environments
- Looking to mature beyond basic vulnerability scanning
- Seeking measurable risk reduction
This makes TEM a high-quality, decision-stage topic—ideal for ranking against competitors that still focus on traditional models.
How Organizations Can Get Started with TEM
- Start with continuous asset visibility
- Break down silos between security tools
- Prioritize exposures based on exploitability, not volume
- Use attack paths to guide remediation strategy
- Measure success by reduced exposure, not number of alerts closed
Organizations are changing the way they view Cyber Risk. Not only are attack surfaces expanding but threats themselves are also becoming targeted, so therefore Security Programs must too evolve with them.
Moving from an Alert-Driven, Reactive defense to an Intelligence-Led Proactive Reduction of Risk, Threat Exposure Management is the epitome of this evolution. For organizations that truly want to reduce Real-World Cyber Risk in 2026 and beyond, Threat Exposure Management is no longer optional; it is foundational.
Frequently Asked Questions
1. What is Threat Exposure Management (TEM)?
TEM focuses security teams on real risk by indicating which weaknesses an attacker can realistically exploit, and where to address first, instead of listing an endless list of issues.
2. How does TEM differ from Vulnerability Management?
Unlike traditional vulnerability management, which focuses on what is wrong, TEM focuses on what could actually be used in an attack. TEM correlates vulnerabilities, misconfigurations and access risks together to provide real-world attack paths.
3. Why does Threat Exposure Management Incorporate A.I?
Due to the rapid changes in modern environments, it is not feasible to perform manual analysis to maintain an accurate understanding of the environment; therefore, A.I. is used to assist with continuously discovering assets, providing context and highlighting the most immediate exposure to threat risk.
4. Why is Threat Exposure Management Vital in 2026?
Due to the overwhelming number of Alerts that are sent to security teams, the growing intelligence of attackers has made it critical for security teams to transition from reactionary measures based on alerts to proactive protective measures that helps in true risk.
Reduce Real Cyber Risk with AI-Powered TEM
Get a risk-focused exposure review, attack path analysis, and a remediation plan that prioritizes what attackers can actually exploit.
Talk to CyberCube