
Following all of the steps outlined by the regulatory framework will provide a sense of accomplishment like getting through audits, completing your forms, showing your certificates, but if you think that compliance equals protection, you are missing the larger point. Compliance is a means by which to fulfil an obligation to meet the legal requirements and industry specifications, but it is not a guarantee of protection from the continuously changing landscape of cyber threats. To keep your data, your company and your reputation safe, it is essential to understand that compliance is the minimum required to define your security posture; you must go beyond compliance.
Let us explore what is involved in compliance, explore how far beyond compliance security goes and explore ways in which to establish a real-world cyber defense that is fit for reality, not just for passing an audit.
Free Security Gap Review
Identify what compliance misses and get a prioritized plan for real-world protection.
What Is Compliance in Cybersecurity?
Think of compliance as the rulebook. It’s about adhering to the standards & regulations defined by government entities and corporate bodies for those in a certain industry. These rules represent the minimum expectation for how to safeguard your confidential data including customer credit card numbers, health information of patients, or other personal identifying information.
The following are some common compliance frameworks you may be familiar with:
GDPR (General Data Protection Regulation) - Protects privacy rights of individuals within the European Union.
HIPAA (Health Insurance Portability and Accountability Act) - Provides regulations to ensure the safe keeping of personal health information in the United States.
PCI DSS (Payment Card Industry Data Security Standard) - Sets the ground rules for handling payment cards securely.
ISO/IEC 27001 - An international gold standard for information security management.
What’s the main purpose of compliance? To show that your organization is being responsible and to avoid penalties. Auditors will check if you’ve got the basics covered: firewalls, secure access, encryption, and more. In essence, compliance is about answering, “Are we doing what the rules say we should?”
Need Audit-Ready Evidence?
We help map controls to evidence and reduce last-minute audit pressure.
What Is Security Beyond Compliance?
Now let’s flip the page. Security is where the real work begins. Security is about staying one step ahead of hackers, scammers, and even careless mistakes. It’s a daily commitment to protecting everything that matters most in your business.
Security beyond compliance is a deeper level of security that requires a different mindset and focuses on the following core areas of action:
Proactive Threat Hunting – instead of waiting for alerts about threats, take the initiative to actively seek out threats before they occur.
Real-Time Monitoring and Response – detect problems when they occur and stop them as soon as possible.
Adversary Emulation – think like a hacker and identify vulnerabilities before the hacker does.
Security-First Culture – ensure that everyone in your organisation knows what their role is in defending your business.
So, the big question security asks is “If a determined attacker comes knocking, are we ready to handle it?” If you can answer “yes” to that, you’re moving beyond basic compliance to true resilience.
Make Security Continuous
Move from annual checklists to ongoing monitoring and risk reduction.
Difference Between Compliance and Security
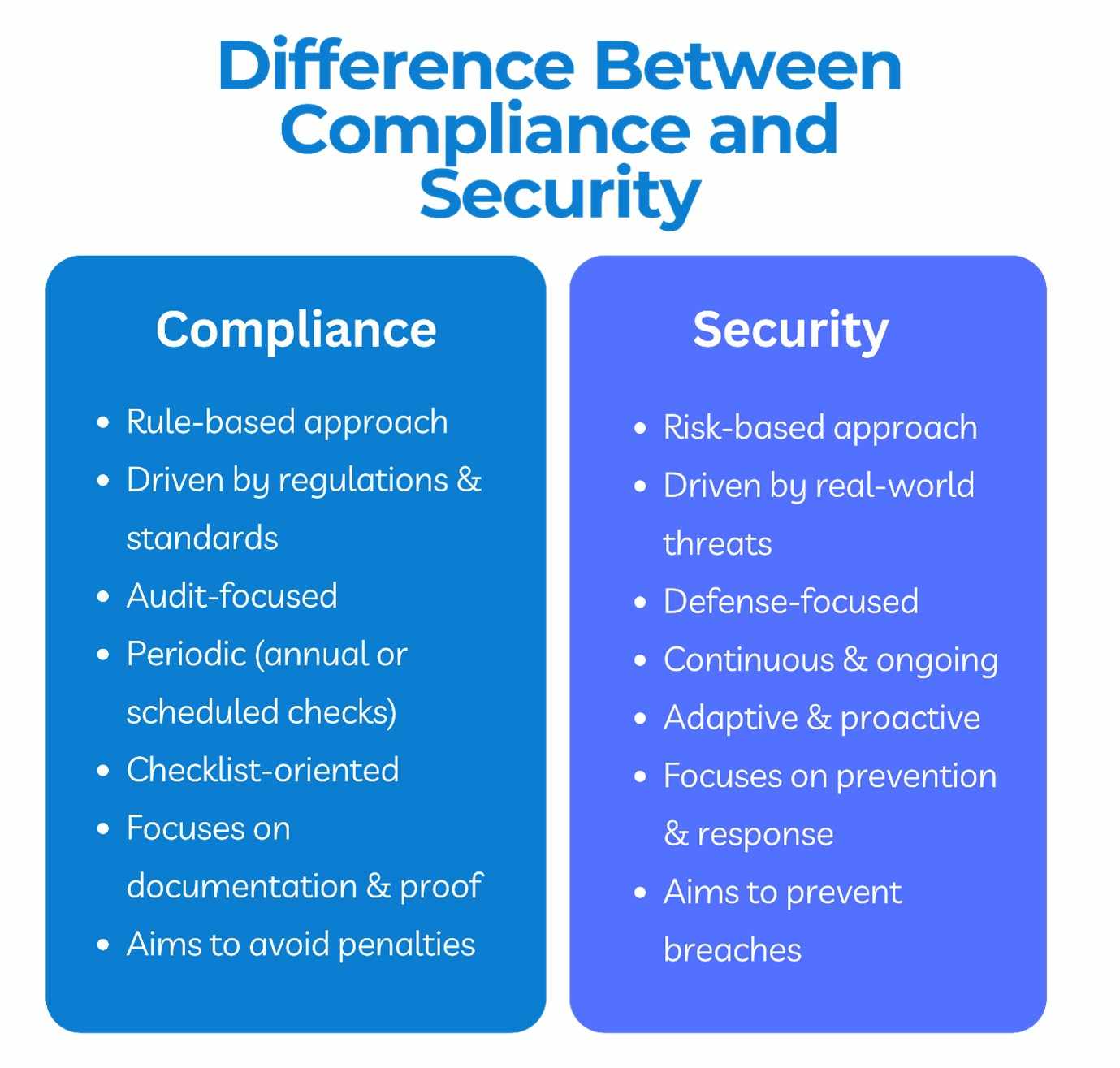
Compliance is an annual check-up. Security is a habit that you do every day. And yes, you can be fully compliant and still have some overlooked risks because no ruleset can think of every threat out there.
Why Compliance Alone Is Not Enough for Cybersecurity
It’s tempting to lean on compliance. After all, those standards are put together by smart people and help you avoid legal trouble. But here’s the harsh truth: regulations change slowly, and attackers move fast. If you only focus on passing the annual audit, you’ll always be a few steps behind the bad guys.
Compliance Is a Checklist, not a Defense
Compliance asks “Do you have controls?” but doesn’t always check how well those controls work for your unique organization. You might have a firewall in place, but if it isn’t set up right for your situation, it’s just a box ticked, not actual protection.
And because most compliance frameworks lag behind new threats, your defenses can quickly become outdated, even if your paperwork is up to date. Modern attackers love to exploit this gap.
Attackers Do Not Follow Compliance Rules
Here’s something often forgotten, hackers don’t care about your compliance report. They look for cracks in your armour, especially in places compliance missed. Social engineering attacks, phishing, vendor breaches, these are all areas that a checklist cannot always cover.
Also, once the audit is over, many organizations ease off on security, just when attackers are most likely to pounce.
Real-World Examples Where Compliance Failed
Some of the most talked-about data breaches in history involved companies that were technically compliant.
Target (2013): Fully PCI DSS compliant. Still, over 40 million cardholders were affected by a massive breach because attackers accessed the network through a third-party vendor—something compliance didn’t dive deep into.
Equifax (2017): On paper, they had their regulatory requirements covered. But they left a known software vulnerability unpatched, and that let hackers steal the data of nearly 150 million people.
The takeaway? Compliance keeps you on the right side of the law, but not always on the right side of a cyberattack.
How to Build Security Beyond Compliance
- Adopt a Zero-Trust Security Model: Assume your network could be hacked by both external threats as well as internal ones so you will not allow employees and vendors to enter your organisation's premises without validating their identity first.
- Continuous Monitoring and Path Detection Technology: By implementing new technologies in your organisation, you will have a constant watchful eye that will alert you as soon as a security incident occurs.
- Regular Security Awareness Training of Your Employees: Your employees are your company's first line of defence; by providing them with frequent security awareness training that is applicable to their jobs, you can help ensure that security remains a top priority for your entire workforce.
- Be Prepared to Respond to Incidents: plan prior to the occurrence of incidents, it is more likely than not that incidents will happen, so forming and practicing your organisation's incident response plan in advance allows the organisation to be more ready for an incident should one occur.
- Conduct Risk Assessments on a Continuing Basis: Your risk assessments must be based on the risk profile of your organisation versus simply relying on a generic risk assessment or audit templates. The assets, threats and priorities of your organisation are all unique and distinct from other organisations.
Compliance is a Minimum Standard of Protection
Compliance is fundamental for building and sustaining an organization’s ongoing success because it is the evidence of an organization’s commitment to protect Consumers’ Data and Privacy. Compliance does not represent the same level of risk and it does not protect an organization from different forms of Cybercrime and Cybersecurity threats; it only provides a level of assurance to the Organizations’ Clients and Customers that there is a high level of effort being put towards protecting their information from attack or compromise. Cybercrime continues to grow.
FAQs
-
How do Compliance and Security differ from one another?
Compliance represents a process of putting policies and procedures in place to prevent an organization from facing legal or regulatory issues, whereas Security is the ongoing development of Strategic Business Strategies to mitigate the Risk of Cybercrime and protect the Organization and Consumers’ Data from Cybercrime.
-
Can an organisation be Secure without meeting Compliance requirements?
However, it is very improbable that this would be the case. The vast majority of Security Best Practices will align with the requirements mandated by Compliance. There have been cases where organisations have successfully complied with all applicable regulations and then experienced a Cyber breach, highlighting the importance of supporting both Security and Compliance initiatives.
-
Why do many companies tend to emphasise compliance more than they do security?
Due to Compliance being easily measurable and the possible penalties for non-compliance, there is generally a more significant urgency to establish compliance Until an organisation has experienced a Cyber breach closely, there is little chance of an understanding of the measurable aspects of Security.
-
How can Small Businesses improve their cybersecurity?
One key way for Small Businesses to upgrade their Cybersecurity options is to take care of the fundamentals; starting with the need to create Passwords that meet an acceptable Complexity Level; establishing Multi-Factor Authentication; creating Employee Training to Educate Employees on how to avoid phishing or Ad scams, create Backup plans, ensure that Software Updates are done, identify what data is most important to protect. Start implementing the right policies and procedures today. Your organisation will thank you in the form of a better sense of security and peace of mind.
Build Security Beyond Compliance
Get a risk-focused security assessment, continuous monitoring guidance, and a practical roadmap that goes beyond audit checklists.
Talk to CyberCube