
Cybersecurity has never been static, but 2026 is shaping up to be the year when the entire industry shifts. The systems we protect are changing, the people who use them are scattered across hybrid workplaces, and the attackers targeting them are now armed with tools that operate faster than humans can blink. For years, organisations relied on fixed perimeters, predictable threat patterns, and annual security audits — but that world doesn’t exist anymore. Threats continue to change and adapt at a rapid pace and businesses that will be able to thrive will be those businesses which continue to adapt and change along with them.
The reason we are now seeing this display of changing threats in the form of AI-based attack methods and other AI threats is due to the rapid evolution of technology itself. As we approach 2026, three key factors are driving change within today's global security environment and considering many are interconnected and often dependent upon each other. Companies have to take into account the resurgence of the concept of using 'protecting the perimeter' as an effective means of providing security in today's threat landscape.
Traditionally, when focusing on perimeter protection, organisations would rely on physical security measures as their main forms of protection. However, as attackers continue to find ways to bypass traditional perimeter protections, organisations must begin focusing on how they are ensuring their security is protected against the various forms of attack that they may face when they do not get in through front door.
This is where Adaptive Cybersecurity steps in — a modern approach that changes just as fast as your environment does. Unlike the old, static models, adaptive security isn’t about reacting to incidents after the damage is done. It’s about continuously sensing, learning, and adjusting your posture so threats can’t gain ground. Think of it as security that doesn’t sleep, doesn’t slow down, and doesn’t assume anything is safe until proven otherwise.
Using AI in Cybercrime to Create New Innovations
A few years ago in cybersecurity, Artificial Intelligence (AI) was primarily employed as an aid for protecting businesses from potential cyber threats through automated alerts, anomaly detection, and predictive threat analysis. However, by the end of 2026, the introduction of AI into the cybercrime industry may have produced more sinister methods used by cybercriminals. Many cyber attackers today leverage large language models as well as synthetic media tools to develop highly sophisticated phishing emails that very closely resemble the writing, style, and overall personality of a legitimate person.
Deepfake voice calls sound like actual executives. Malware no longer stays the same for more than a few seconds — it mutates automatically, making signature-based detection nearly useless.
The shift isn’t that attackers have become more intelligent — it’s that their technology has. What used to require a seasoned cybercriminal can now be executed by someone with minimal skills and a clever AI script. This has widened the threat landscape and erased the margin of error that organisations once enjoyed.
To illustrate how dramatically these attacks have evolved, take a look at the comparison below:
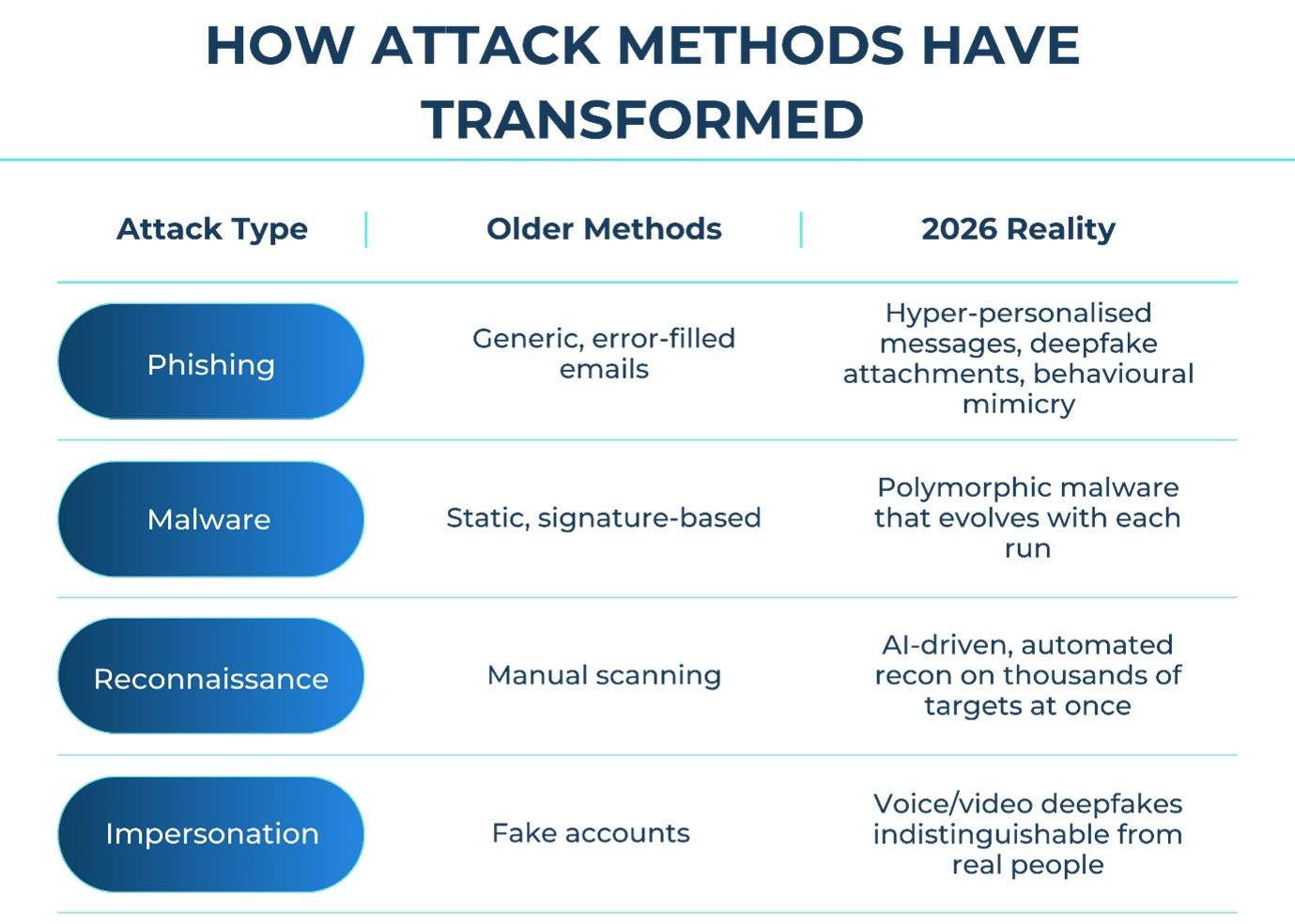
AI-powered threats don’t wait for working hours. They don’t get tired. And they don’t stick to a script. That’s why defending against them requires systems that can learn and adapt just as quickly.
The Silent Breach: Supply-Chain Attacks Are Now the #1 Entry Point
The most significant attacks on organisations over the past few years have not been originated from the internal systems of the organisation but rather came from outside influences. It has become increasingly necessary for organisations to develop complicated digital ecosystems with multiple third-party services and products (including cloud-based systems, Software as a Service (SaaS) tools, open-source libraries, payment processors, remote developers, and office equipment). All of these services and products contribute to an organisation's digital supply chain; however, the strength of the digital supply chain of an organisation is only as strong as its weakest link.
Since 2026, attackers have discovered that it is more effective for them to compromise smaller vendors and use the vendor's access credentials to gain entry into dozens of companies that are more valuable than the smaller vendor they compromised. Compromise of a plugin update, a hacked API key or the misconfiguration of an integration can allow a cybercriminal to access previously secure information. These types of attacks are particularly dangerous because they can appear to be legitimate traffic, since the compromised requests originate from trusted providers of services, rather than from potential threat actors.
Organisations often say they trust their security. But can they trust every vendor’s security? Every contractor’s laptop? Every SaaS tool integrated into their internal workflows? That’s where the real risk lies.
Hybrid Work Isn’t a Trend — It’s a Permanent Attack Surface
The hybrid work culture, once considered a temporary adaptation, is now part of the global operating model. Teams work from offices, homes, cafés, coworking spaces, and sometimes countries with far fewer cybersecurity standards. Devices move across networks every day. Files shift between personal machines and enterprise systems. Employees install productivity tools that IT teams don’t even know exist.
This fluid environment has created an attack surface that grows daily and doesn’t stay still long enough for traditional monitoring tools to track. One misconfigured AWS bucket, an overlooked remote login, or an unpatched home router is all it takes.
Why Traditional Cybersecurity Models Fail in 2026
For years, cybersecurity revolved around firewalls, VPNs, antivirus software, and one-time assessments like annual VAPT. These were effective when environments were predictable. But they weren’t designed for AI-driven phishing, supply-chain infiltration, or hybrid micro-mobility.
Static defences follow a pattern. Attackers don’t.
That gap is exactly where organisations lose ground.
Adaptive Cybersecurity: The Only Sustainable Strategy for Today’s Environment
Adaptive cybersecurity is not a tool but a mindset. It considers security to be an ongoing process of understanding, evaluating, and responding. The philosophy is straightforward: your security controls must change as quickly as the people trying to break into your networks and as the environments in which you work.
Instead of waiting until something happens, you must evaluate everything as it happens by utilising current information, behavioural analysis, automatic monitoring, and continuous verification to prevent anything from getting to the point of becoming a breach.
Let’s consider this in practice:
-
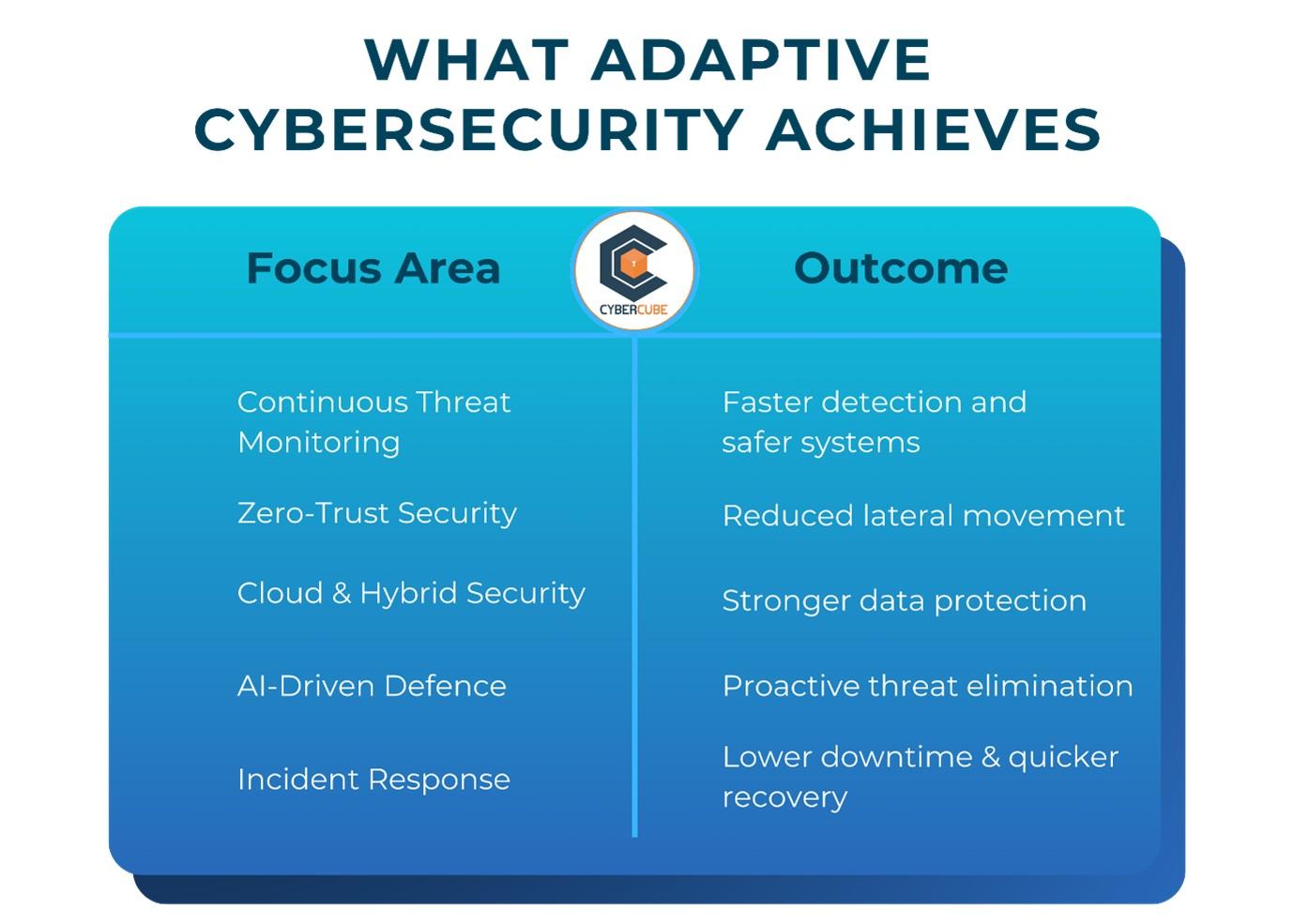
Ongoing Assessments of Risks & Threats
Annual audits are outdated. Cyber threats are constantly changing and so organisations require an ability to see how cyber threats and risks evolve. Cyber risks are now assessed using ongoing tools, including vulnerability mapping (to reveal where a company is most exposed), credential scanning (to find out where an exposed credential exists), misconfiguration identifying (to highlight where a misconfigured credential is), and monitoring for any unusual activity (that may lead to further dangerous activity). All of these methods help organisations to keep their knowledge of the threat landscape progressive and current based on the attack surface.
-
Zero-Trust as a Default Setting
Zero-trust isn’t just a framework — it’s a philosophy that says:
“We trust nothing without verification, not even internal traffic.”Every access request is validated. Every device is authenticated. Every identity is continuously monitored. Zero-trust micro-segmentation ensures that even if an attacker breaks in, they can't move freely inside the network. It’s like putting every room behind its own locked door.
-
Securing the Hybrid & Cloud Environment
Cloud systems evolve daily. New services are added, rights are changed, integrations expand, and configurations shift. Without automated cloud posture management, organisations can’t keep up. Modern cloud security tools not only detect risky configurations but automatically remediate them before attacker’s notice.
-
AI-Driven Threat Monitoring
AI doesn’t just power attacks — it also powers defence. Modern security systems use machine learning to detect subtle behavioural anomalies that humans would miss. Unusual login times, unfamiliar access routes, abnormal data movement — all of these are detected within seconds. Automated response systems can isolate impacted systems instantly, reducing breach impact dramatically.
-
Resilience Through Strong Incident Response
Even with perfect security, incidents happen. The organisations that recover fastest are the ones with clear, well-tested incident response plans. This includes ransomware playbooks, vendor compromise protocols, automated disaster recovery, and employee awareness training. Resilience is not about preventing every attack — it’s about minimizing damage and bouncing back stronger.
A Quick Summary: What Adaptive Cybersecurity Achieves
2026 is not a year of incremental cybersecurity improvements — it’s a year of transformation. The businesses that continue to exist will not be determined by their many policies or the size of their firewalls; they will be the ones who embrace and completely change their view on what security is all about.
Adaptive Cybersecurity means you have a willingness to continue to grow, remain vigilant, as well as acknowledge that the speed and nature of today's cyber-world is not going to get slower than it is now.
Businesses that adopt this mentality today will be the most resilient, secure, and future-ready in the years to come.
Get Ready for Adaptive Cybersecurity
We’ll help you design and implement an adaptive cybersecurity strategy that covers AI threats, supply-chain risk, and your hybrid workforce.
Talk to CyberCube